As cyber threats evolve, we constantly hear new terms for attacks such as DoS, DDoS, and DrDoS, but many people find it confusing to understand the differences between them.
In this post, we will help you understand each type of attack, how they affect your network, and how they are different from one another.
We’ll also explain the basics of DoS and DDoS attacks, show how to detect and protect against them, and describe the unique features of DDoS attacks.
By the end of this article, you’ll have a clear view of how these attacks work and how you can protect your systems from them.
Let’s get started!
Table of Contents
- 1 What is a DoS Attack?
- 2 What is a DDoS Attack?
- 3 What is a DrDoS Attack?
- 4 Difference Between DoS vs DDoS vs DrDoS
- 5 How to Detect DoS Attacks
- 6 Protecting Your Server with RunCloud
- 7 Final Thoughts
- 8 FAQ on DoS vs DDoS vs DrDoS
- 8.1 Which attack is more serious, DoS or DDoS?
- 8.2 Are DoS attacks always intentional?
- 8.3 What is the difference between a brute force attack and a DoS attack?
- 8.4 What is a DoS attack with an example?
- 8.5 Is a DoS attack illegal?
- 8.6 Can you stop DDoS attacks?
- 8.7 Does CAPTCHA prevent DoS?
- 8.8 Can IDS prevent DOS attacks?
- 8.9 What is an example of a DDoS attack?
What is a DoS Attack?
A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. The primary goal of a DoS attack is to render the target system inaccessible to legitimate users, effectively “denying service” to those who need it.
If you think DoS attacks are uncommon, you should know that Cloudflare, a popular cloud provider, reports that in 2023, they blocked 14 million DDoS attacks.
That’s not 14 million requests – it’s 14 million separate attacks, with each attack possibly consisting of hundreds of millions of malicious requests.
Types of DoS Attacks
DoS attacks come in various forms, each with its own method of overwhelming the target system:
- Volume-Based Attacks: These attacks attempt to consume all available bandwidth of the target system.
- Protocol Attacks: These exploit vulnerabilities in network protocols to exhaust server resources.
- Application Layer Attacks: These target vulnerabilities in web applications and services.
Examples of DoS Attacks
SYN Flood
A SYN Flood attack takes advantage of the TCP handshake process by sending a large number of SYN requests to a server. These requests initiate a connection, but never complete it, exhausting the server’s resources. This overwhelms the server’s ability to process legitimate requests, potentially causing a denial of service.
Ping of Death
The Ping of Death attack involves sending oversized ICMP packets to a target system. When the target tries to reassemble these fragmented packets, buffer overflows can occur, resulting in system crashes or unexpected behavior. This exploit takes advantage of vulnerabilities in how systems handle large packets.
HTTP Flood
An HTTP Flood attack targets web servers by overwhelming them with a massive number of HTTP requests. By sending continuous and numerous requests, the attacker consumes server resources, potentially leading to slow performance or complete downtime. This type of attack mimics normal web traffic, making it difficult to detect and block.
Slowloris
The Slowloris attack maintains many open connections to a target web server, keeping each connection alive as long as possible. By sending partial HTTP requests, the server’s resources are tied up in trying to handle these incomplete requests, leaving fewer resources available for legitimate traffic. This method effectively disrupts server operations without requiring high bandwidth.
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is similar to a DoS attack as it also tries to overwhelm the target infrastructure with a flood of Internet traffic.
However, unlike a Denial of Service (DoS) attack, which uses a single computer and Internet connection, a DDoS attack uses multiple computers and Internet connections, often distributed globally in what is referred to as a botnet.
These botnets are distributed globally, making it extremely difficult to pinpoint and block the sources of the attack.
For example, Dyn suffered from one of the largest recorded DDoS attacks in 2016. The attack used the Mirai botnet, which consisted of numerous compromised Internet of Things (IoT) devices. By sending an overwhelming amount of traffic to Dyn’s servers, the attack disrupted major websites and online services, including Twitter, Netflix, and Reddit, causing significant outages across the United States and Europe.
Similarly, in 2023, security researchers found a vulnerability in the HTTP/2 protocol which allowed attackers to create very large DDoS attacks. This vulnerability lets attackers easily overload web servers, making websites slow or unavailable. Since this was a new kind of attack, numerous websites across the internet were disrupted due to traffic spikes.
Suggested read: 8+ Security Tips to Secure VPS Server in 2024
What is a DrDoS Attack?
A Distributed Reflection Denial of Service (DrDoS) attack, also known as a Reflected DDoS attack, is a more sophisticated form of DDoS attack.
In a DrDoS attack, the attacker spoofs the victim’s IP address and sends requests to a large number of reflectors (such as DNS servers or NTP servers). These reflectors then send their responses to the victim, overwhelming their network.
DrDoS attacks are particularly dangerous due to their amplification factor. A small amount of attack traffic can generate a much larger volume of attack traffic directed at the victim. This makes them both more difficult to trace back to the original attacker and more devastating in their impact on the target.
In 2021, Cloudflare stopped a huge DrDoS attack that reached almost 2 terabits per second (Tbps) by using its strong security systems. This attack used different methods, such as UDP floods and DNS amplification, to try to overwhelm the target’s network. Although this attack was unsuccessful, it was one of the biggest attacks observed to date and could have done serious damage.
Types of DrDoS Attacks
DrDoS attacks can be categorized based on the protocol or service they exploit:
- DNS Amplification: This technique exploits DNS resolvers to send a large volume of DNS response traffic to a target. By sending small queries with a spoofed source IP address (the target’s address) to these resolvers, the attacker causes them to send amplified responses to the target, overwhelming it with traffic.
- NTP Amplification: This type of attack Exploits Network Time Protocol (NTP) servers to flood a target with traffic. Attackers send crafted requests to NTP servers with the target’s IP address, which causes the servers to respond with a significantly larger volume of data.
- SSDP Amplification: This method takes advantage of the Simple Service Discovery Protocol, commonly used by Universal Plug and Play (UPnP) devices, to overwhelm a target with traffic. Attackers send discovery requests to devices with the target’s spoofed IP address, which causes these devices to send their responses directly to the target, multiplying the traffic load.
- Memcached Amplification: This approach uses improperly configured memcached servers to generate extremely large traffic volumes aimed at a target. By sending small requests with a forged IP address, attackers can cause the servers to respond with enormous payloads, massively amplifying the attack traffic directed at the target.
Difference Between DoS vs DDoS vs DrDoS
While DoS (Denial of Service), DDoS (Distributed Denial of Service), and DrDoS (Distributed Reflection Denial of Service) attacks all aim to disrupt services, they differ in their execution and impact.
Here’s a brief comparison:
|
Aspect |
DoS |
DDoS |
DrDoS |
|
Source |
Single attacking system |
Multiple attacking systems |
Multiple intermediate systems |
|
Scale |
Generally smaller |
Large scale |
Potentially massive scale |
|
Complexity |
Simpler to execute |
More complex |
Highly sophisticated |
|
Detection |
Easier to detect and mitigate |
More challenging to mitigate |
Very difficult to trace and mitigate |
|
Traffic Amplification |
No amplification |
No amplification |
Significant traffic amplification |
|
Example |
SYN Flood from a single source |
Botnet attacks from multiple sources |
DNS Amplification attack |
How to Detect DoS Attacks
Although researchers use advanced traffic monitoring and anomaly detection systems to reliably detect a DoS attack, there are several simple things that you can monitor to detect DoS attacks on your website:
- A sudden spike in network traffic can indicate a DoS attack, as attackers flood the server with excessive requests to overwhelm its resources. Monitoring tools can help detect these abnormal traffic patterns and allow you to respond quickly before they affect service availability.
- A noticeable slowdown in server response times may signal that the server is struggling to process a large number of incoming requests.
- Unusual patterns in incoming requests, such as repeated access attempts from a single IP or strange request types, can indicate a DoS attack. Analyzing logs and traffic data can help identify these anomalies, allowing you to implement measures to block or filter out malicious traffic.
- High CPU or memory usage on your server, especially during non-peak hours, can be a sign of a DoS attack. You can use server monitoring tools such as New Relic to track your resource usage.
Protecting Your Server with RunCloud
Setting up a secure server can be tough, but RunCloud makes it easy.
When you use RunCloud to create a new server, you immediately benefit from several security features automatically:
- Fail2Ban: This tool helps prevent brute-force attacks by temporarily or permanently banning IPs that show malicious signs.
- Auto-Updates: RunCloud automatically updates your server’s software and applies necessary security patches to protect it 24/7.
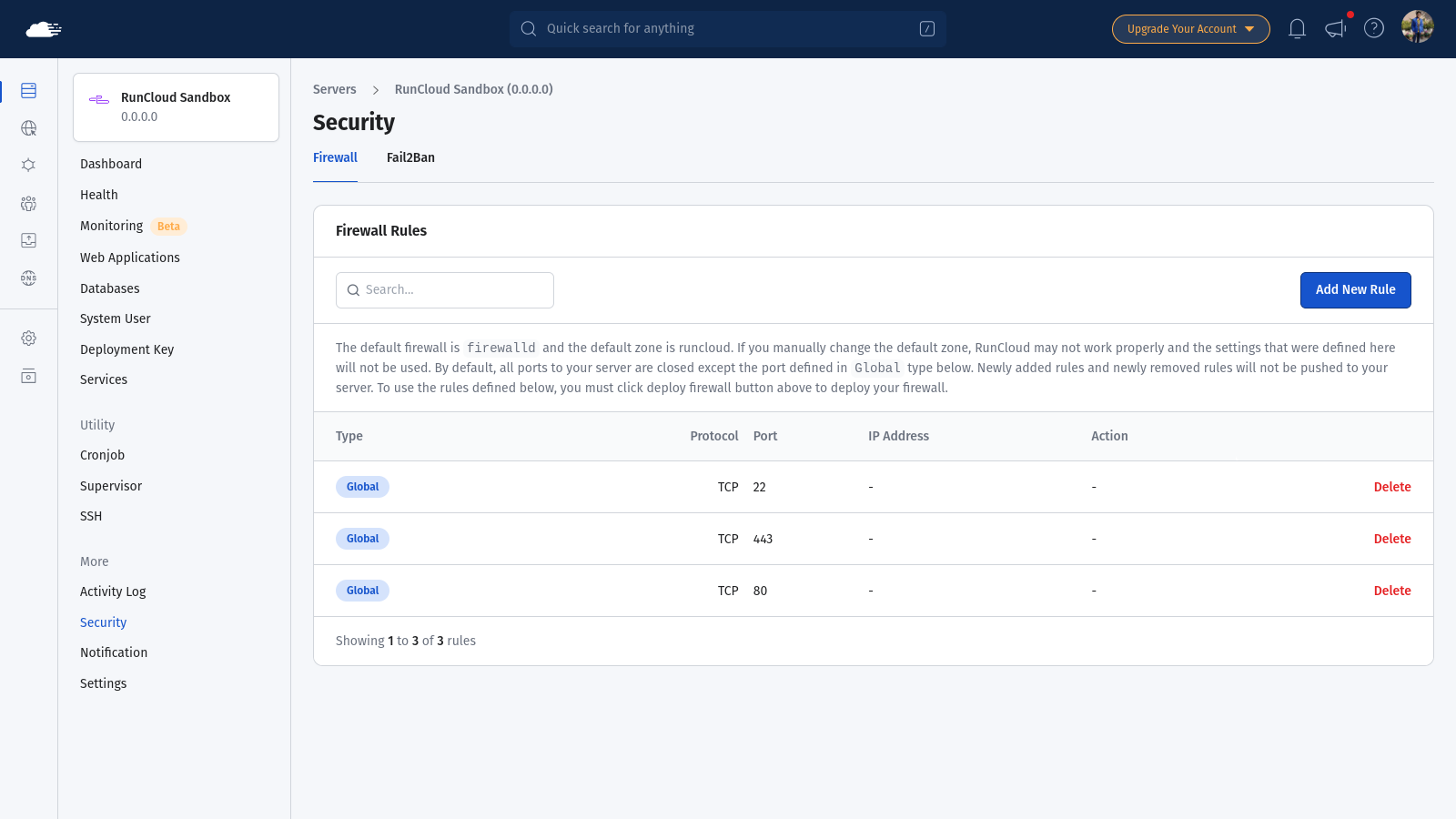
- Firewall: RunCloud automatically closes unnecessary ports that hackers might try to use – this reduces the attack surface significantly. The firewall also protects your server from various attacks, including DoS attacks. Here’s what the WAF does:
- Rate Limiting: Prevents a single IP address from making too many requests in a short time.
- Request Filtering: Blocks requests that look suspicious or dangerous.
- IP Blacklisting: Automatically blocks computers that show malicious behavior.
These features work together to keep your server safe in real-time. This means you can focus on your work without worrying about attacks.
Adding Custom Firewall Rules on RunCloud
If the default security settings are not enough for you, you can enhance your website’s security by adding custom firewall rules. This feature allows you to precisely control incoming traffic by filtering requests based on various parameters such as Cookie, Country, Hostname, IP Address, URI, and more. By configuring these rules, you can fine-tune your security settings to block or allow specific types of traffic.
For example, you might want to block traffic from certain IP addresses or countries, or allow requests only from specific hostnames.
To implement this, open your web application dashboard in RunCloud and then navigate to Firewall > Add Firewall Rule.
On this page, use the custom rule interface to set conditions like:
When incoming requests match…
- Field: Hostname
- Operator: equals
- Value: e.g.,
example.com
Then…
- Action: Allow, Block, or Disable Rule
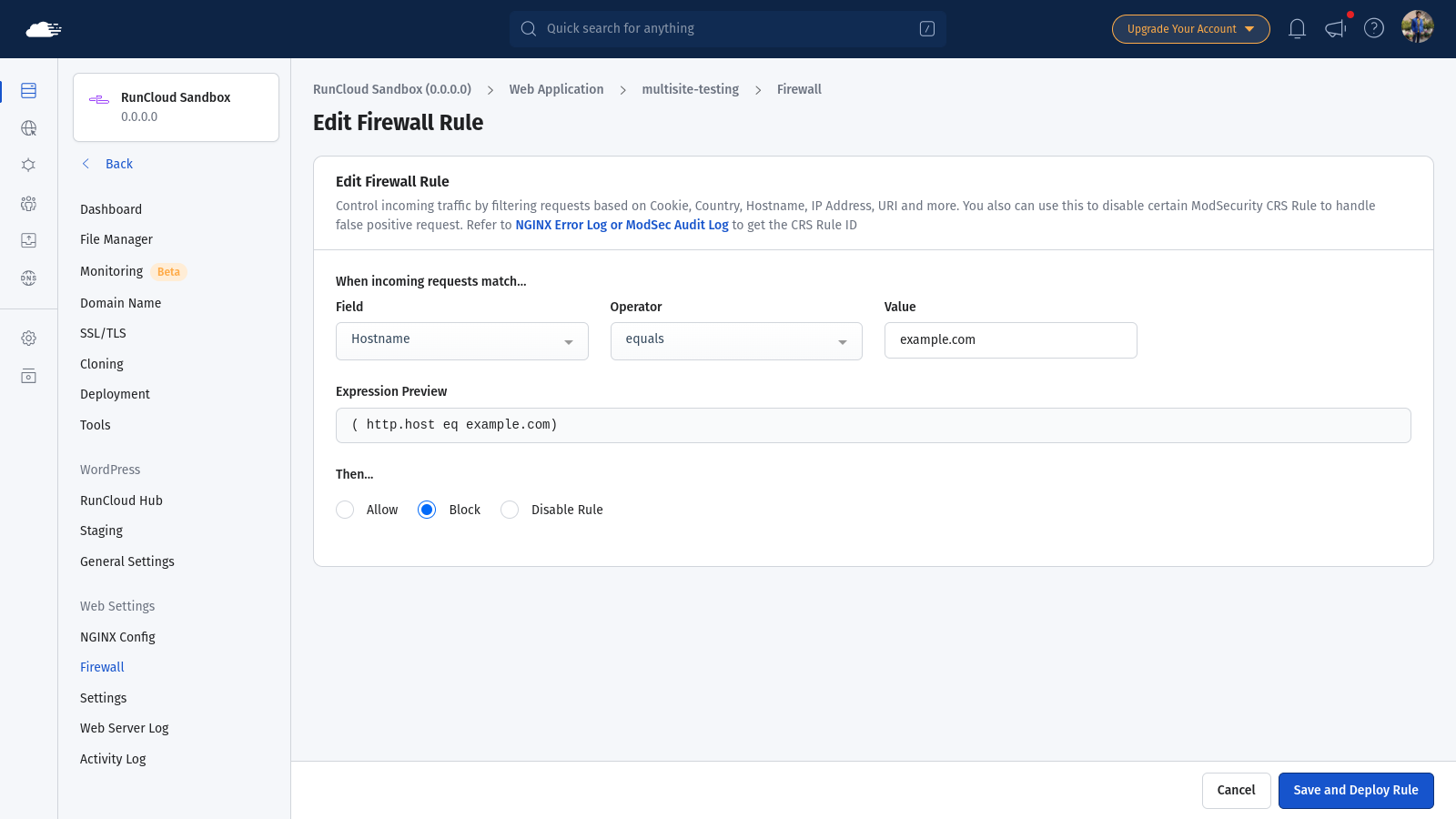
Once you have modified the settings, you can click on “Save and Deploy Rule” to add this firewall rule to your server.
Want to learn more about how RunCloud keeps your server safe?
Check out these helpful blog posts:
- How to Use Cloudflare Firewall Rules to Protect Your Web Application
- How To Use ModSecurity and OWASP CRS For Web App Firewall To Secure Your Website
- Configure Fail2ban and Firewalld on RunCloud
- How To Use Fail2ban With WordPress And Cloudflare Proxy
Final Thoughts
In our research for this article, which highlights how DoS and DDoS attacks can cause significant damage to websites and online services, we were shocked to discover that 1 in 25 Cloudflare survey respondents indicated that DoS attacks were carried out by state-level or state-sponsored threat actors.
By following the suggestions provided in this article, you can quickly detect and fend off many basic DoS attacks. However, if you need something more sophisticated, then you should sign up for RunCloud.
With RunCloud, you’re not just getting a control panel – you’re getting peace of mind.
You can sleep well at night knowing your server is in good hands. RunCloud is always working to keep your server safe, updated, and running smoothly.
Start using RunCloud today!
FAQ on DoS vs DDoS vs DrDoS
Which attack is more serious, DoS or DDoS?
DDoS attacks are generally considered more serious than DoS attacks. This is because they use multiple sources, making them harder to mitigate and potentially causing more severe disruptions due to their larger scale and complexity.
Are DoS attacks always intentional?
No, DoS attacks are not always intentional. While many are deliberate, some can occur due to configuration errors, unexpected traffic spikes, software bugs, or hardware failures that mimic DoS effects.
What is the difference between a brute force attack and a DoS attack?
Brute force attacks aim to gain unauthorized access by guessing passwords or encryption keys. DoS attacks, on the other hand, attempt to make a service unavailable by overwhelming it with traffic or exploiting vulnerabilities to exhaust system resources.
What is a DoS attack with an example?
A DoS attack attempts to make a computer or network resource unavailable to its intended users. An example is a SYN flood, where an attacker sends many SYN packets with spoofed IP addresses, overwhelming the server with half-open connections.
Is a DoS attack illegal?
Yes, in most jurisdictions, DoS attacks are considered illegal. They’re typically classified as a form of cybercrime under various laws such as the Computer Fraud and Abuse Act in the United States.
Can you stop DDoS attacks?
While it’s challenging to completely prevent DDoS attacks, their impact can be mitigated. Strategies include traffic analysis and filtering, bandwidth expansion, cloud-based protection, and using web application firewalls (WAF).
Does CAPTCHA prevent DoS?
CAPTCHA can help mitigate certain types of application-layer DoS attacks by preventing automated bot attacks. However, it’s not effective against network-layer attacks and should be used in conjunction with other security measures.
Can IDS prevent DOS attacks?
An Intrusion Detection System (IDS) can help detect DoS attacks but typically can’t prevent them alone. For effective prevention, IDS should be combined with other tools such as firewalls and intrusion prevention systems (IPS).
What is an example of a DDoS attack?
A notable example is the Mirai Botnet attack in 2016. It used a massive network of compromised IoT devices to launch a DDoS attack that caused widespread internet outages across North America and Europe.