I Ditched Claude Code and Now Using Open Source Qwen AI for Real Sysadmin Work
Borg is a powerful, fast, and reliable solution that is also very explicit, and forgetting even a single flag can affect the end result in ways you didn’t intend to….
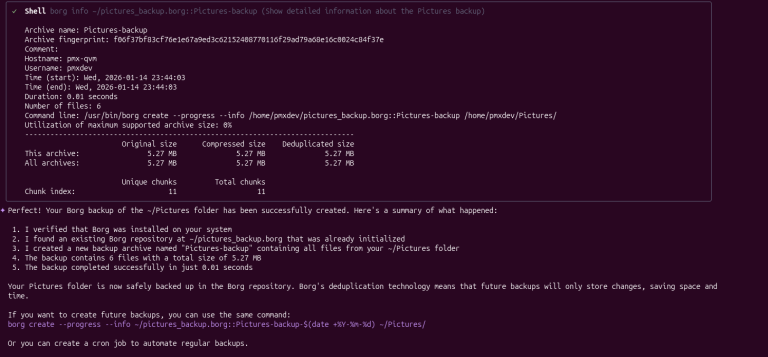
Borg is a powerful, fast, and reliable solution that is also very explicit, and forgetting even a single flag can affect the end result in ways you didn’t intend to….
Get-Service docker Check the Docker CLI: Run the following command to verify that the docker command is available in your system’s PATH. Suggested read: Self-Hosting Docker vs Cloud-Based Docker Legacy…

In this video, I walk through how to run Docker on Proxmox the right way and avoid the common mistakes that can break your home lab setup. Proxmox is an…
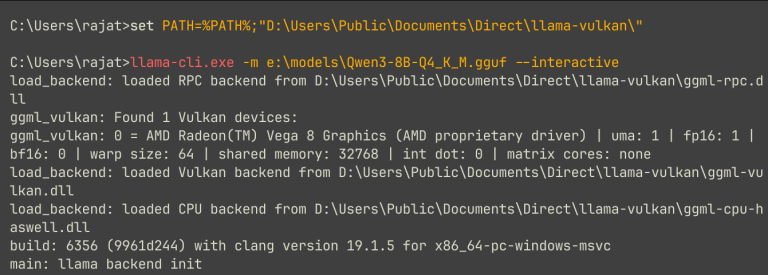
I started with the usual tools, i.e., Ollama and LM Studio. Both deserve credit for making local AI look plug-and-play. I tried LM Studio first. But soon after, I discovered…
For now, we are using the format %I:%M %p, that will show the time as 12:30 PM. Example of top panel in Xfce Another useful options are the mouse-click items….
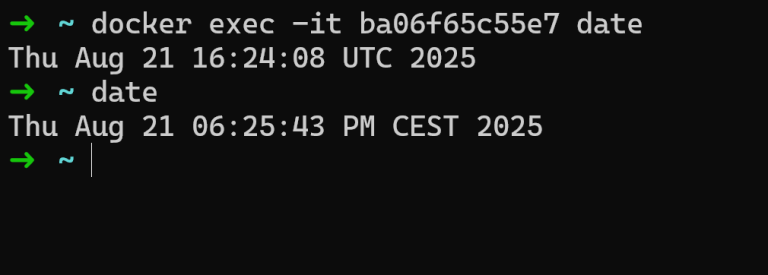
docker exec -it my-web-app /bin/bash Running Database CLI Tools: You need to inspect a database running inside a container. To do so, you can exec into the container and use a command-line client like psql or…
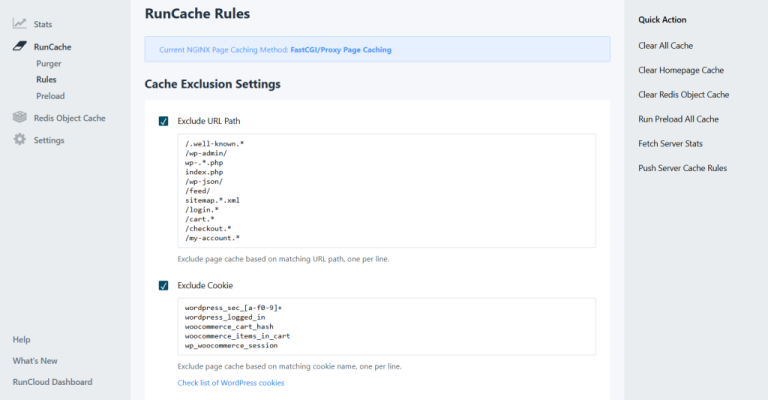
Here is a simple and effective ruleset to add to your .htaccess file:The warning is triggered for two main reasons:Adding expiration headers is very straightforward, especially in the .htaccess file…
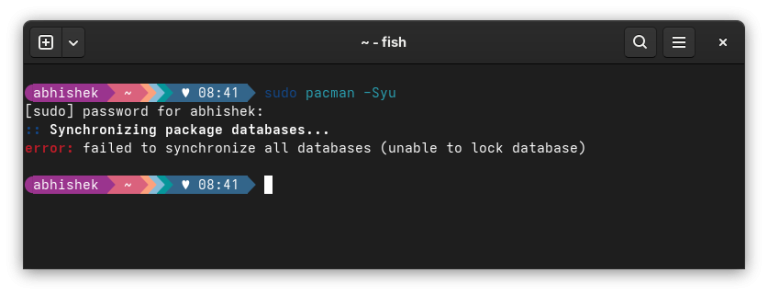
If it did, drop a quick “Thank You”. That is a motivation booster.Here’s a screenshot of the entire scenario on my CachyOS linux: Handling failed to synchronize all databases error…

Secure Boot is a security standard developed to keep your computer safe from malware that could sneak in and start doing harmful things even before the operating system (OS) fully…
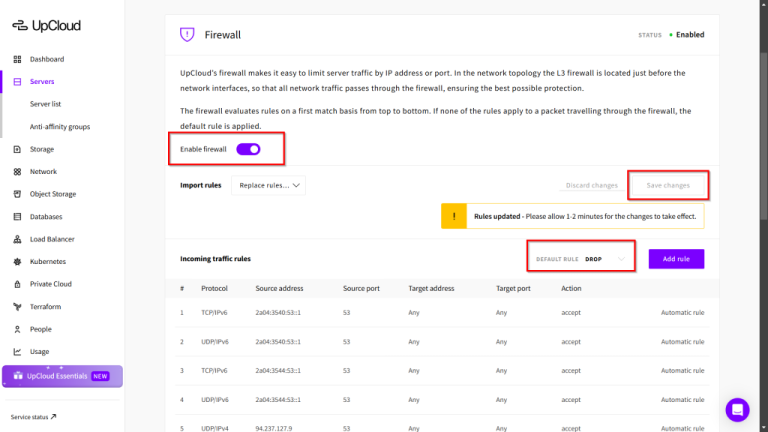
UpCloud uses its own proprietary MaxIOPS storage technology to deliver industry-leading performance and reliability. It’s claimed to be faster than SSD – built on enterprise-grade SSDs, but up to 2x…
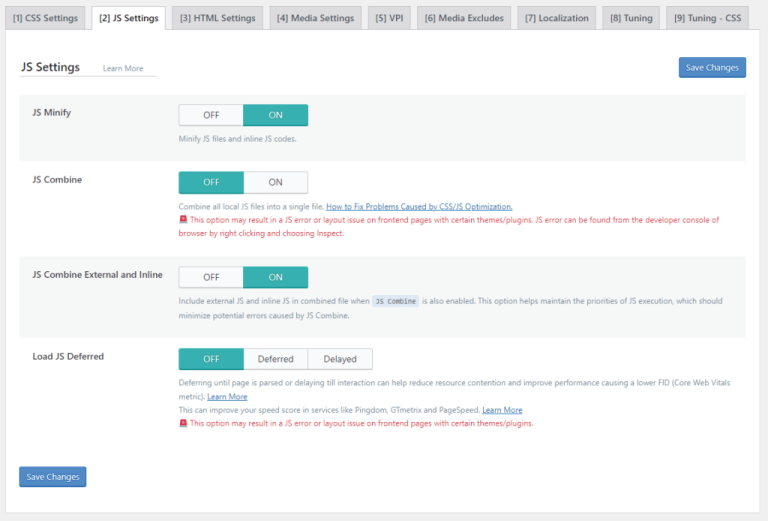
In this article, we will walk through the steps of installing the LiteSpeed plugin on your WordPress site and explain how to configure it correctly.It’s important to note that the…
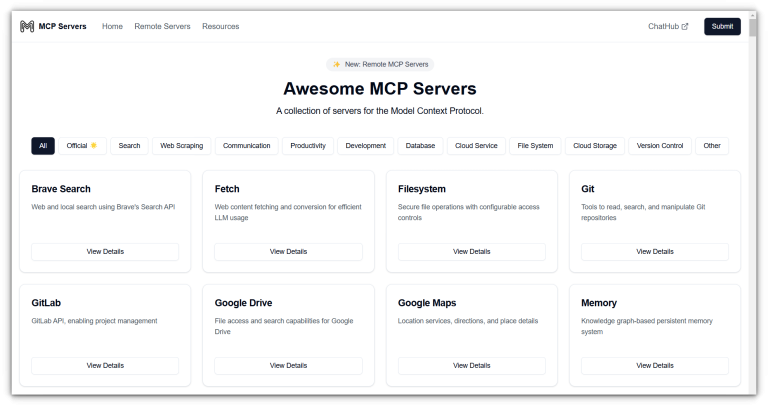
Each part of the system has a clear role, contributing to a modular and scalable environment for AI integration.MCP stands for Model Context Protocol, an open standard introduced by Anthropic…

In this guide, we’ll decode what those LED signals mean and how to use them effectively in your troubleshooting process.📋This means the diagnostic capabilities are slightly less extensive, but the…
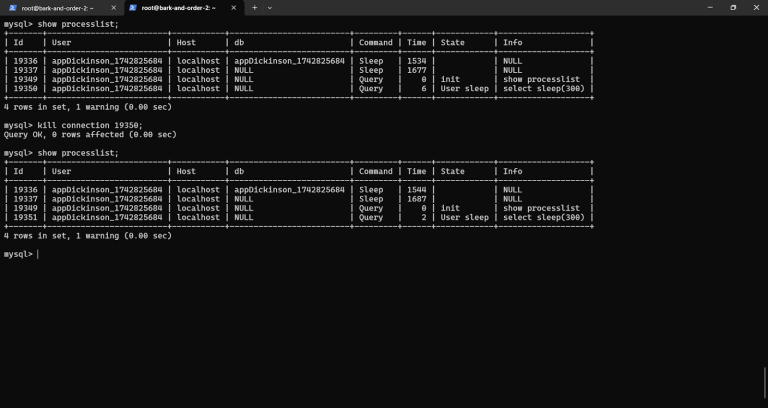
mysql -u root -p Step 5: Verifying the KillAfter running this command, you’ll be prompted to enter a password. Paste or type the MySQL root password you retrieved from your RunCloud dashboard….
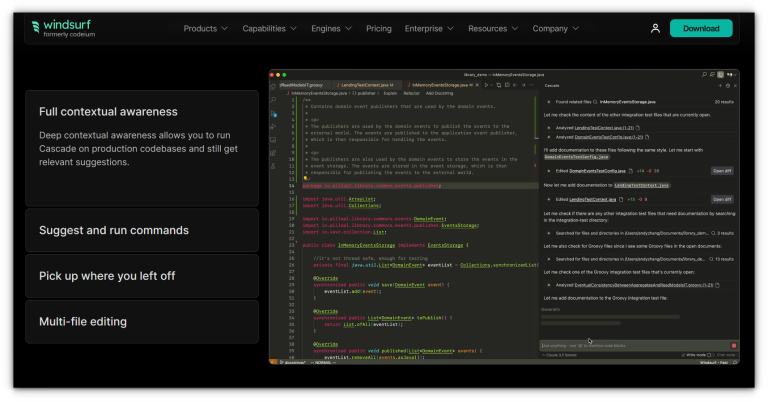
✅ Built entirely in Rust for extreme performance and low latency.✅ Native AI support with inline edits, slash commands, and fast refactoring.✅ Assistant Panel for controlling AI interactions and inspecting…
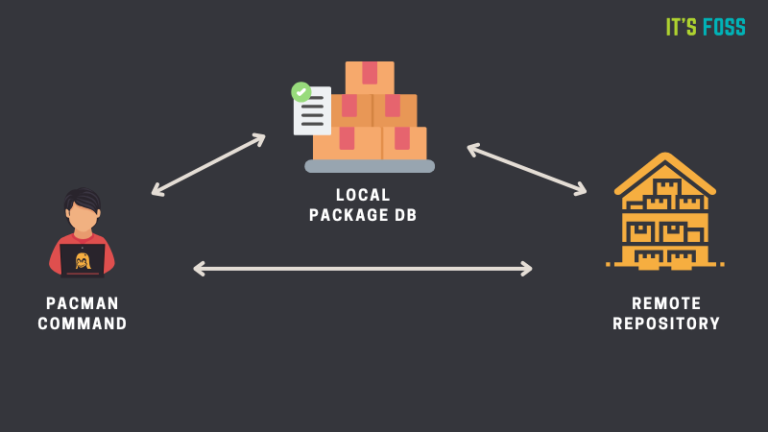
You cannot just run pacman -S and expect it to sync (install) all the packages from the repositories on the local system. That would be disastrous if your system installs…
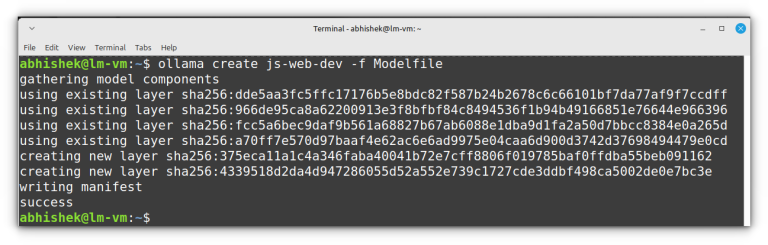
I feel that this should be enough to get you started with Ollama, it’s not rocket science. My advice? Just fiddle around with it. ollama run llava:7b “Describe the content…
Run this command to make it executable.Curl is a tool that deals with URLs and indeed requires those system calls.Utilizing Libc Cosmopolitan, she was able to port OpenBSD Pledge to…