11 Alternatives To reCAPTCHA to Protect Your Site from Spam
For most users, the proof of work is invisible and fast, but for suspicious users or regions, it becomes harder and longer. Proof of work can protect against brute force…
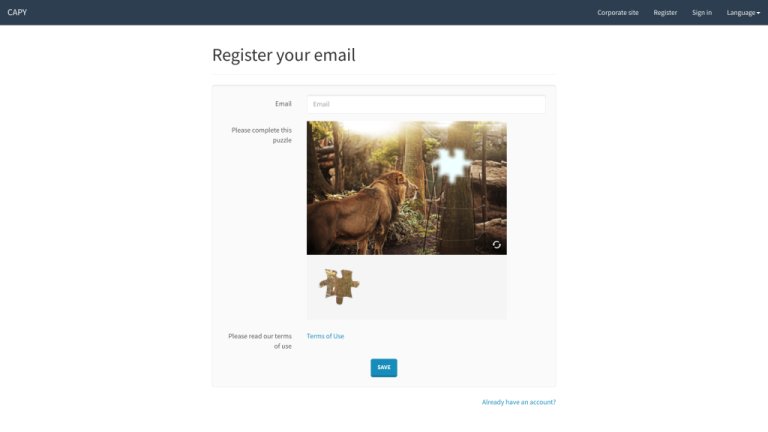
For most users, the proof of work is invisible and fast, but for suspicious users or regions, it becomes harder and longer. Proof of work can protect against brute force…
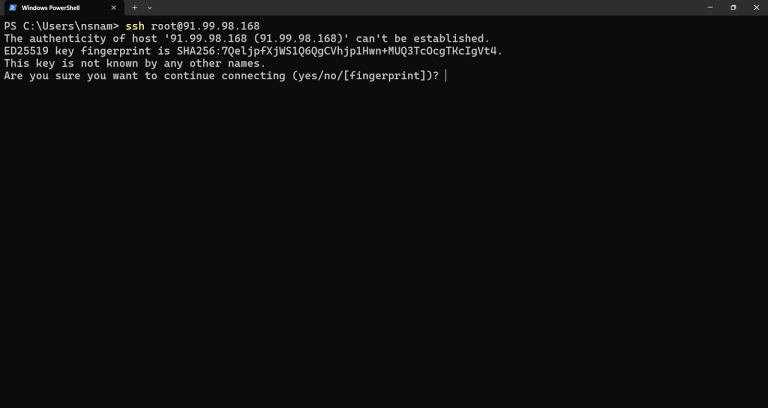
In this post, we have seen that the “Warning: Remote host identification has changed” error is an important security mechanism that is doing its job. By following the steps in…
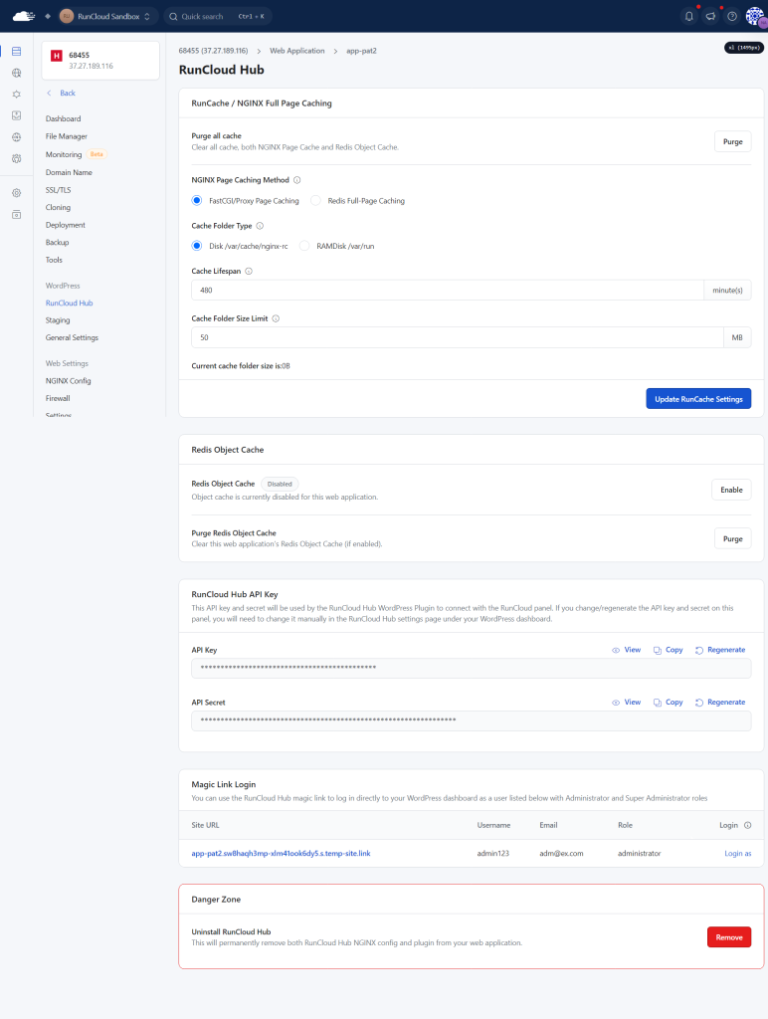
NGINX is exceptionally well-suited for high-traffic sites due to its event-driven architecture and efficient resource utilization. Its ability to handle thousands of concurrent connections with minimal resource overhead makes it…
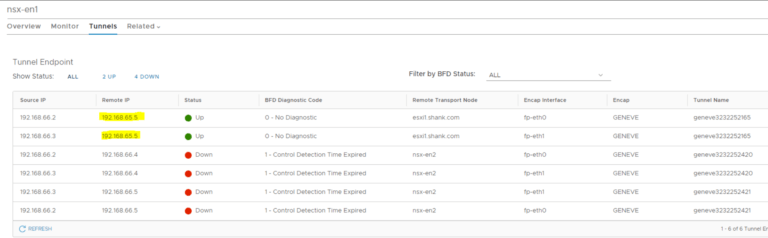
In NSX-T 3.0 the edges require an active BFD session in order to remain in an up/active state. When you have two edge virtual machines in a cluster, they create…
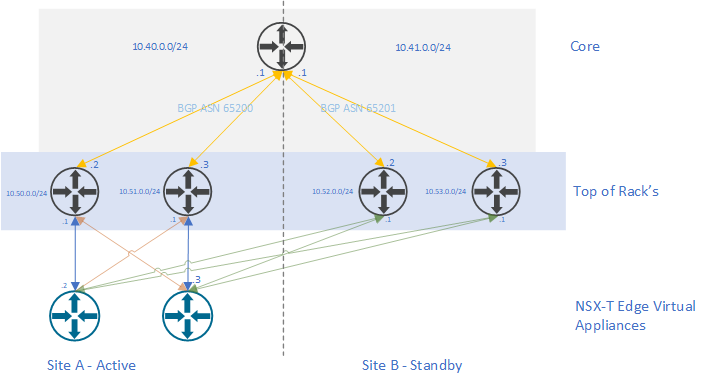
September 18, 2020 Multisite Deployment of NSX-T Data Center Part 1| LAB2PROD NSX-T Active-Active Multisite in a Single Region and Failover to a Secondary Region Part 1. A client required…
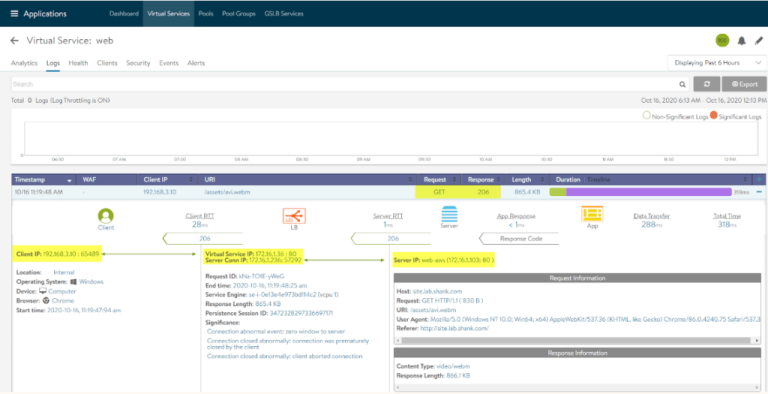
October 12, 2020 Multi-Cloud GSLB using NSX Advanced Load Balancer|LAB2PROD A guide to configuring a Global Server Load Balancer (GSLB) between an on premise NSX-T enabled datacenter and Amazon Web…
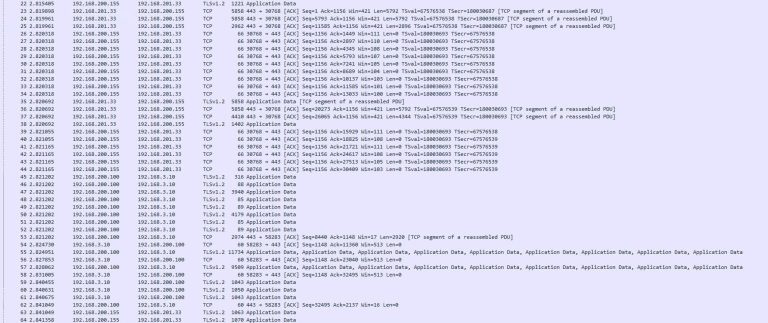
January 12, 2021 SSL Termination: Securing Web Traffic with NSX-ALB | LAB2PROD Leverage NSX-ALB to encrypt your data with SSL Termination! In this blog post we will cover the different…
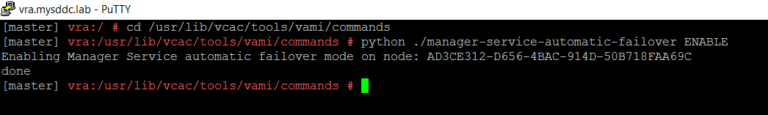
Upgrading vRA solution has been always tricky as it is version dependent. Although the process is somehow similar, it may include less or more steps if you have a minimal…