How to Set Up a Hetzner Server to Host Your Websites
After the installation is complete, you can type ‘exit‘ in PowerShell to close the connection to the server. You can type ‘exit’ again to close the PowerShell window as well.Finally…
After the installation is complete, you can type ‘exit‘ in PowerShell to close the connection to the server. You can type ‘exit’ again to close the PowerShell window as well.Finally…
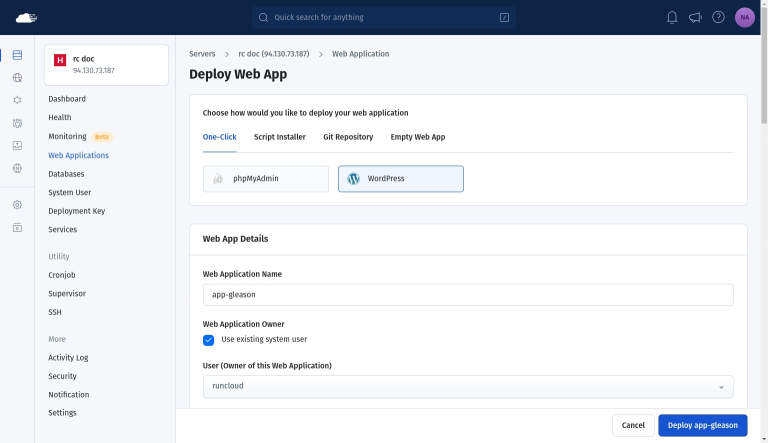
Choose based on your budget, location, and technical comfort. RunCloud works seamlessly with all of them.No guesswork. No wasted time.RunCloud excels at configuring, managing, and securing the server that hosts…
It’s safer than allowing anonymous comments, significantly reducing bot spam, but it doesn’t eliminate the threat entirely, as bots can automate registration. To stop fake user signups, you should also…
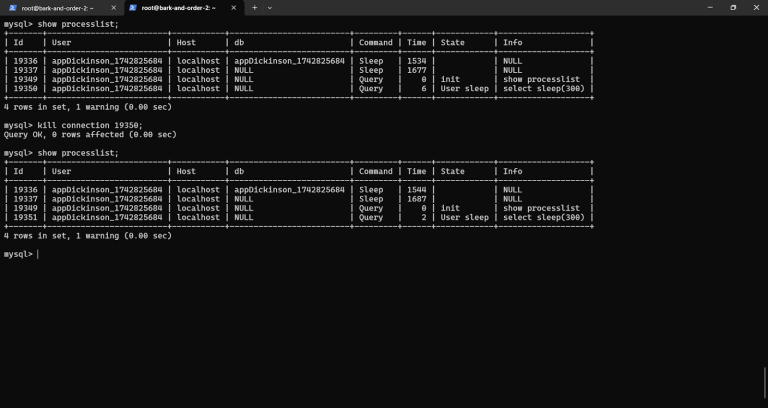
mysql -u root -p Step 5: Verifying the KillAfter running this command, you’ll be prompted to enter a password. Paste or type the MySQL root password you retrieved from your RunCloud dashboard….
Yes, RunCloud is beginner-friendly without sacrificing power. The dashboard is intuitive, the setup processes are automated, and tasks like SSL setup, backups, and app deployment are simplified, making it accessible…
If you prefer using a visual interface instead of typing commands, you can use the Podman Desktop application on Windows, macOS, and Linux. This app gives you a single screen…
sudo ./vendor/bin/sail artisan migrate sudo ./vendor/bin/sail root-shell In addition, Dockerization brings significant benefits in terms of isolation, scalability, and resource efficiency for Laravel projects. Each Docker container runs in its own isolated userspace, preventing conflicts…
To minimize the impact of downtime, you can consider deploying once a day on weekdays outside of peak hours. This schedule can be configured easily using the GitHub action itself. In…
Understanding the often complex pricing models of different providers requires careful attention. You might also experience “vendor lock-in”, where moving your setup from one cloud provider to another becomes difficult…
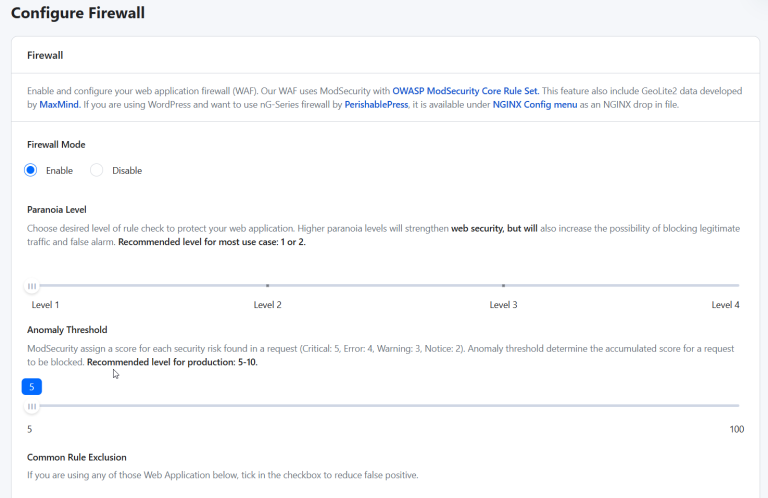
Vulnerability scanners primarily detect weaknesses rather than directly prevent attacks; they act like an early warning system. Preventing attacks requires you to act on the scan results by patching vulnerabilities, using…

Think of your .htaccess as the blueprint for your security system. When exposed, it reveals exactly which files you’re protecting, which directories you’ve restricted, and what specific countermeasures you’ve implemented….
![How to Use FTP to Upload Files to WordPress Without Password [Step By Step]](https://vmme.org/wp-content/uploads/2025/03/how-to-use-ftp-to-upload-files-to-wordpress-without-password-step-by-step-18-768x427.png)
Whether you’re a beginner blogger or a seasoned developer, mastering FTP can unlock a new level of control over your WordPress website. Stop relying solely on the WordPress dashboard –…
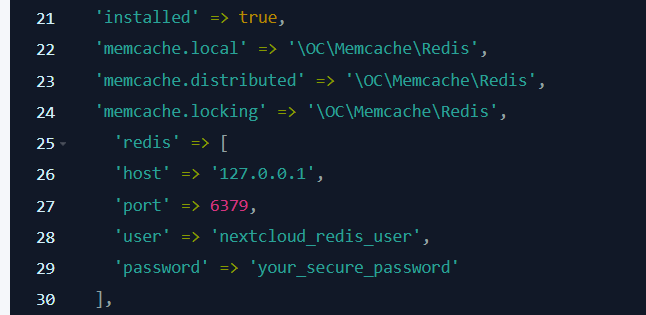
After deploying the application you will need to download the NextCloud installation file to your server. There are two ways to do this.You can configure these parameters to add or…
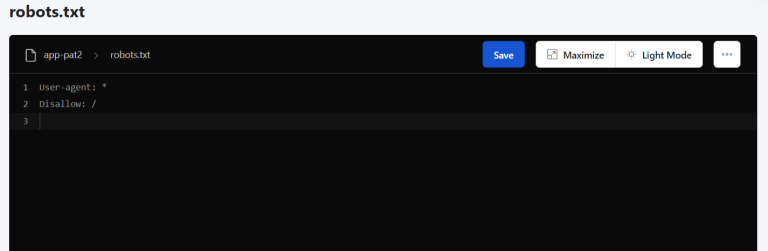
While editing the robots.txt file directly without a plugin can be more technically involved, it offers some distinct advantages for advanced users and those who prefer greater control over their…
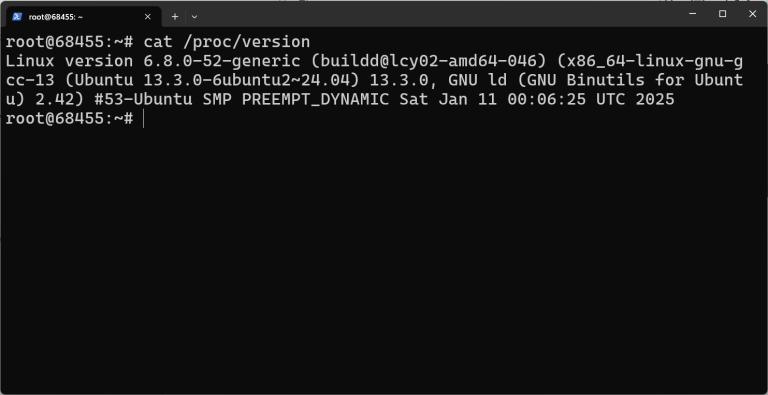
The command cat /etc/os-release provides comprehensive information about your Linux distribution, including the full OS version and name. Alternatively, lsb_release -a offers detailed distribution-specific information in a user-friendly format.Most Linux desktop environments,…

Modern web hosting providers offer additional services beyond simple storage, including:RunCloud provides complete access to your server resources and doesn’t put arbitrary restrictions on the number of websites, size of your…
Several plugins, like “ThumbPress” or “Disable Generate Thumbnails”, offer user-friendly interfaces for managing and disabling default WordPress image sizes.We handle the server-side optimizations so you can focus on what matters…
Exim isn’t a Mail Transport Agent, so there are some features that you won’t get. For example, it will not store emails and doesn’t support IMAP or POP protocols. However,…