Canonical’s Snap Store is the latest in line, with the platform facing increasingly sophisticated attacks, and a recent development makes things look particularly bleak.Well, much of the matter would’ve been tackled if domain names were bound to their original owners (with the option to transfer them to others) and weren’t left to the bandits once some time limit was up. But that isn’t feasible in today’s time.The tactics have evolved over time. Initially, scammers just published authentic-looking apps with plausible screenshots. When Canonical added text filters, they started using Unicode lookalike characters from other alphabets to bypass detection.
The Snap Store is Due For a Clean-Up
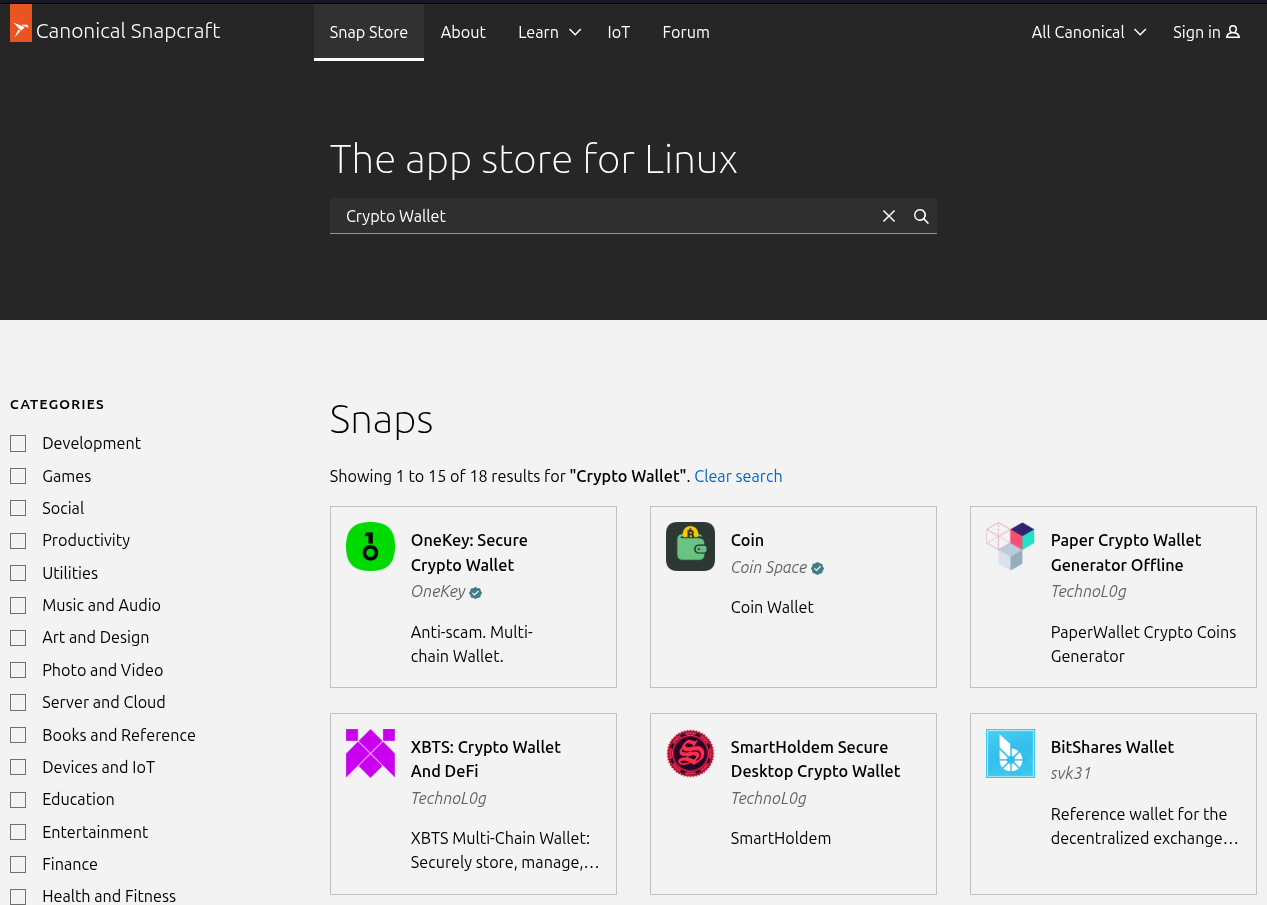
By doing this, they gain control of a legitimate, trusted publisher account with an established history.Before we go ahead, keep in mind that the backend tech for the Snap Store is proprietary, and many people tend to confuse this with Snaps themselves being some mysterious concoction (read: closed-source).Malicious actors are doing everything at their disposal to undermine modern IT infrastructure. Some are motivated by the usual monetary gains, while others have more sinister intents.If they don’t do anything about this, then they are knowingly endangering their users, both private and commercial, you know. 🙃Alan Pope, a former Canonical employee who worked there from 2011 to 2021, has been documenting this mess since early 2024, where fake cryptocurrency wallet applications have been flooding the store.But their latest tactic is utter mischief and absolute deceit. 😑Suggested Read 📖: Check Your Snap Packages for VulnerabilitiesThe scammers have started monitoring the Snap Store for applications whose publishers’ domain registrations have expired. When a domain, let’s say coolproject.tech, is abandoned, these wannabe vultures swoop in to register it in their name and trigger a password reset on the Snap Store account. The next best and obvious bet would be for Canonical to step up their game and do something about this issue. They already have a manual review process for new Snap name registrations, but that isn’t sufficient to handle this particular loophole those sneaky scammers are using, is it?
What Can Be Done?
Then arrived the bait-and-switch approach: publish something harmless like a game under a random name, get it approved, then push a second version containing the harmful malware.Alan was reminded of this long-standing issue when he started monitoring the Snap Store using his SnapScope tool. Though he remains sympathetic to the people working at Canonical and is not angry at the engineers. But he does want the problem fixed.Such scams have led to confirmed losses, including one case where 0,000 was stolen from a single victim.
📋