Fail2Ban traditionally uses iptables or similar firewall backends to implement its banning actions. RunCloud handles all the firewall configurations automatically, ensuring Fail2Ban works perfectly with your server’s firewall setup.sudo systemctl reload fail2ban
Table of Contents
- 1 Final Thoughts
- 2 What is Fail2Ban?
- 3 How to Set Up & Install Fail2Ban on Linux Ubuntu
- 4 How to Configure Fail2Ban
- 5 FAQs on Fail2Ban
- 5.1 What is the difference between Fail2Ban jail.conf and jail.local?
- 5.2 Is Fail2Ban safe?
- 5.3 What is the difference between Fail2Ban and UFW?
- 5.4 How do I ignore my IP address in Fail2Ban?
- 5.5 How do I stop Fail2Ban?
- 5.6 Does Fail2Ban work on SSH?
- 5.7 Is Fail2Ban a WAF?
- 5.8 Does Fail2Ban need iptables?
- 5.9 How much does Fail2Ban cost?
Final Thoughts
RunCloud users don’t need to worry about manually configuring SSH protection as it comes pre-configured with optimal security settings. However, if you want to configure it manually, then you can modify the following parameters in your configuration file as per your requirement:You can easily see all active jails and banned IPs on your server by executing the following command in your terminal:
What is Fail2Ban?
It constantly scans your server’s logs, looking for anyone repeatedly trying to guess passwords or force their way in. While it started as a simple SSH protector, Fail2Ban can be configured to monitor almost everything on your server – from your website traffic to email services and file transfer systems.Millions of servers face relentless attacks daily, but there’s a powerful, free tool that can significantly improve your security: Fail2Ban.But that’s just the beginning of RunCloud’s security features.
Benefits of Using Fail2Ban
sudo fail2ban-client set sshd unbanip 123.123.123.123
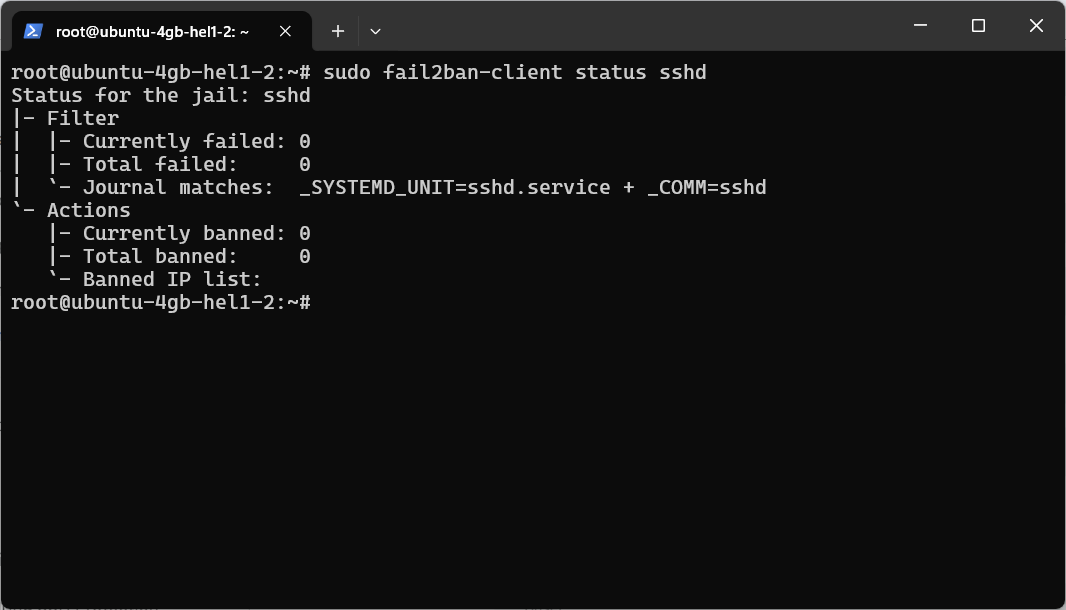
sudo fail2ban-client status sshd
Read our post titled “How to Unban IP Address in Fail2Ban” to get step-by-step instructions.
How Does Fail2Ban Work?
This blocking system works through what technicians call “jails” – separate security rules for different services on your server. Each jail acts like a security checkpoint, with its own set of rules about what’s suspicious, how many strikes before you’re blocked, and how long the timeout should last. You can set up these jails differently for each service according to your requirements.sudo nano /etc/fail2ban/jail.local
Basic Configuration Settings
Fail2Ban is completely free and open-source software. When you use RunCloud, Fail2Ban comes pre-installed and pre-configured as part of your server management package, adding professional-grade security at no additional cost.
How to Set Up & Install Fail2Ban on Linux Ubuntu
sudo apt update
Yes, Fail2Ban excellently protects SSH by monitoring login attempts and blocking suspicious IPs trying to brute force their way in. RunCloud servers come with pre-configured SSH protection through Fail2Ban, providing immediate security against SSH attacks right from the start.
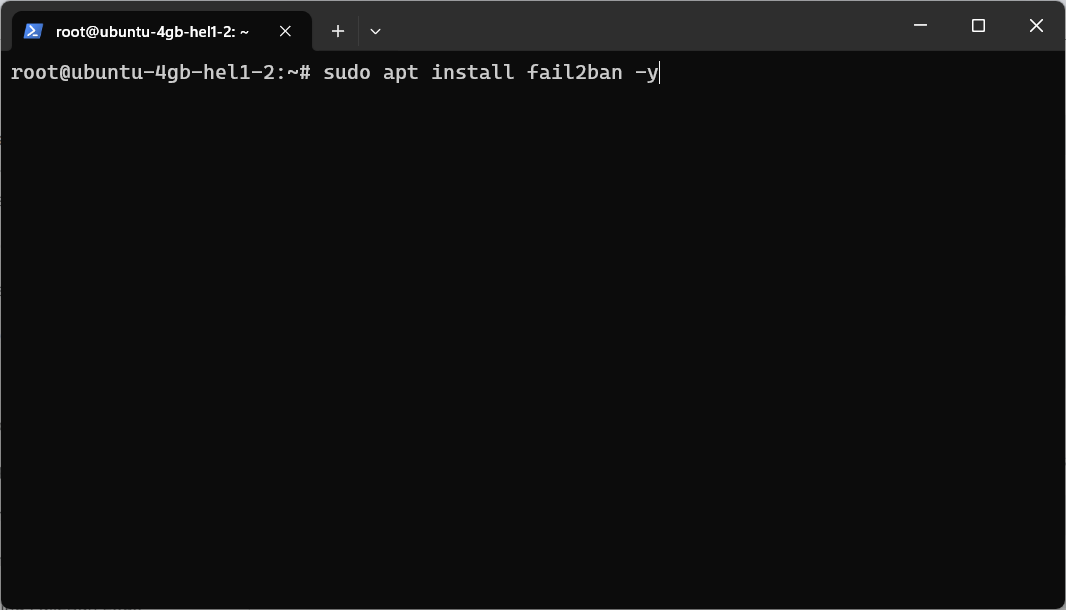
Installing Fail2Ban
sudo apt install fail2ban -y
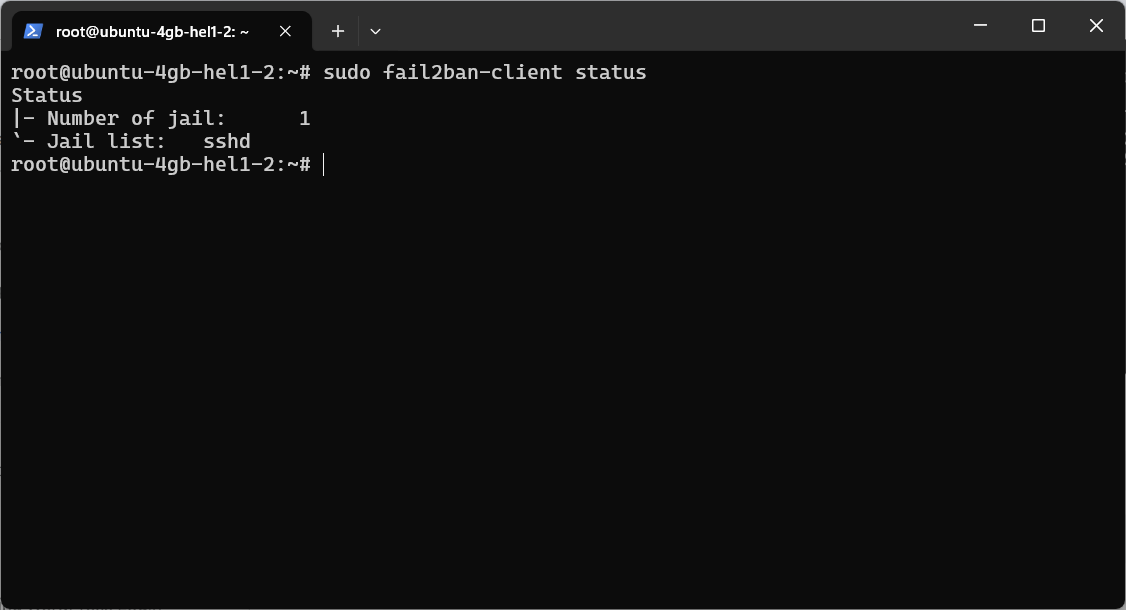
sudo fail2ban-client status
Ready to Secure Your Server?Fail2Ban does its job through a clever but simple process. It reads your server’s log files in real time and scans for things like failed login attempts or suspicious requests. When it spots someone trying to log in with the wrong password too many times, it automatically blocks their IP address using your server’s firewall.But if all of this sounds complicated, you’ll be delighted to know that you don’t need to be a Linux expert to implement robust server security anymore.You can modify SSH jail settings in Fail2Ban to protect your server against brute-force attacks. This method monitors failed login attempts and automatically bans suspicious IPs that exceed the allowed retry limit.Recidive jail is like a “super ban” feature in Fail2Ban that tracks repeat offenders who continue to attack your server even after their initial ban expires. When an IP address gets banned multiple times within a specific timeframe, the recidive jail kicks in and implements a much longer ban duration (usually a week or more) to provide stronger protection against persistent attackers.Suggested read: PHP Security – Best Practices To Secure Your Web App in 2024
Check Active Jails & Banned IPs
Suggested read: PHP Security – Best Practices To Secure Your Web App in 2024
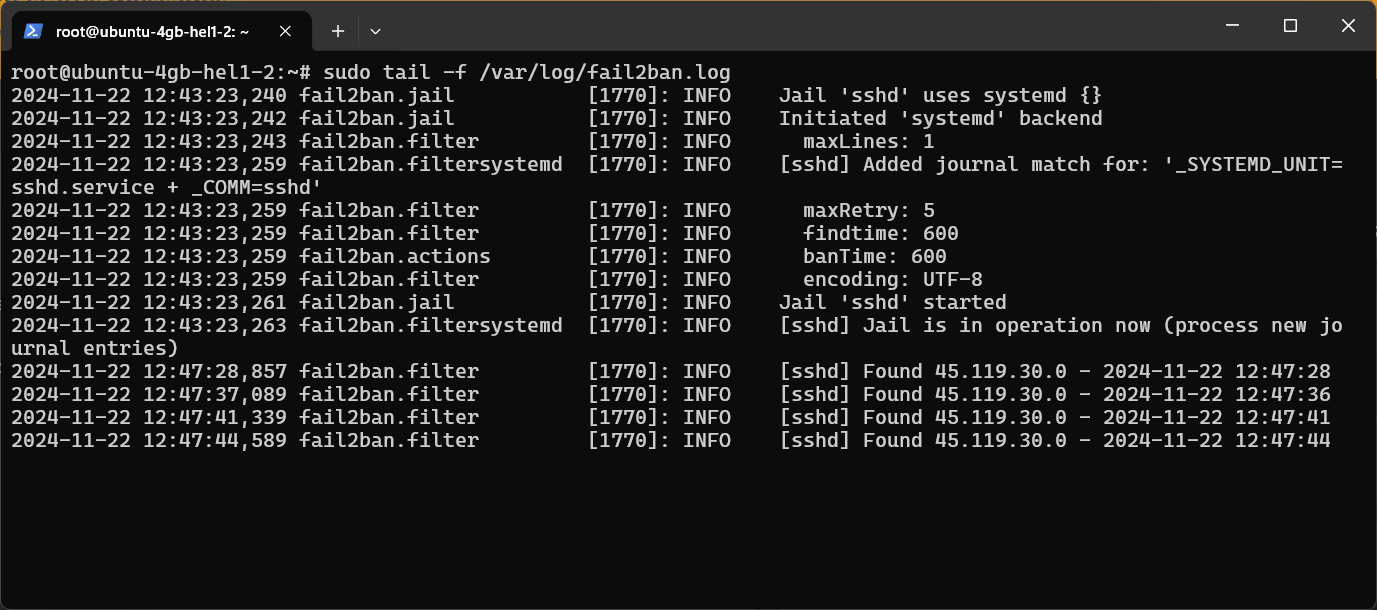
Monitoring Fail2Ban Logs
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
You can view all banned IPs in a specific jail (such as SSH) by executing the following command:
How to Configure Fail2Ban
Fail2Ban is an intrusion prevention system that can block attackers from accessing your server. It can be thought of as an automated bouncer that watches your server’s log files for suspicious activity and kicks out bad actors before they can cause trouble.Suggested read: PHP Security – Best Practices To Secure Your Web App in 2024
Configuring SSH Protection
This comprehensive guide will explore everything you need to know about Fail2Ban, from its basic functionality and installation (on Ubuntu) to more advanced features such as whitelisting IP addresses, as well as its applications for securing various services.Suggested read: 10 Security Tips to Secure VPS Server in 2024? [Ultimate Guide]You can enable it by adding the following code snippet to your configuration file:
Setting Up Multiple IP Ignoring
Note: If you’re using RunCloud, you’re in luck! Fail2Ban comes pre-installed with all RunCloud servers, so you can skip the installation steps and jump straight to configuration.RunCloud makes server security accessible to everyone by including Fail2Ban pre-installed and pre-configured on all servers.[recidive]
enabled = true
filter = recidive
logpath = /var/log/fail2ban.log
bantime = 1w
findtime = 1d
maxretry = 3
Restart/Reload Fail2Ban
To stop Fail2Ban on your server, you first need to log in to it via SSH, and then you can use the command sudo systemctl stop fail2ban in your terminal.Fail2Ban is a dynamic intrusion prevention system that automatically blocks suspicious IP addresses based on their behavior, while UFW (Uncomplicated Firewall) is a static firewall that manages incoming and outgoing traffic based on predefined rules. While they serve different purposes, they work well together, and RunCloud manages both for complete server protection.Think of it as Fail2Ban’s way of saying, “You’ve been warned multiple times, now you’re really not welcome here.”
Enable Recidive Jail
Suggested read: 3 Ways to Fix Too Many Authentication Failures SSH Root? [SOLVED]The jail.conf file contains default settings and gets overwritten during system updates, making it unsuitable for custom configurations. The jail.local file, which takes precedence over jail.conf, is where you should store your custom Fail2Ban settings to ensure they persist through updates.In this section, we will explain how to set up and install Fail2Ban on your Ubuntu server. Start your free RunCloud trial today and experience how easy server management can be. With plans starting from as little as the cost of a dinner per month, you get enterprise-grade security features without the enterprise-level complexity. sudo systemctl status fail2ban
Setting Up the Configuration Files
sudo tail -f /var/log/fail2ban.log
Suggested read: How To Use Fail2Ban With WordPress And Cloudflare Proxy[sshd]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 3
bantime = 24h
No, Fail2Ban is not a Web Application Firewall (WAF) but rather an intrusion prevention system that monitors logs for suspicious activity. For comprehensive security, RunCloud provides both Fail2Ban and additional security features that complement WAF functionality.bantime = 10m # how long to ban an IP
findtime = 10m # time window to look for attempts
maxretry = 5 # number of attempts before ban
Fail2Ban logs provide a real-time window into your server’s security by showing you exactly who’s trying to break in, when they attempted it, and whether they were successfully blocked. You can see these logs by either checking /var/log/fail2ban.log, or you can execute the following command to see the Fail2Ban logs in real time:Using Fail2Ban brings real, practical benefits to your server security as it stops automated attacks by blocking suspicious IP addresses before they can break in. This means your server isn’t wasting time and power dealing with these attacks, freeing up resources to serve other customers and keeping your server fast and responsive for real users.