DevOps Guide For Installing Docker on Windows Server (2016, 2019, & 2022)
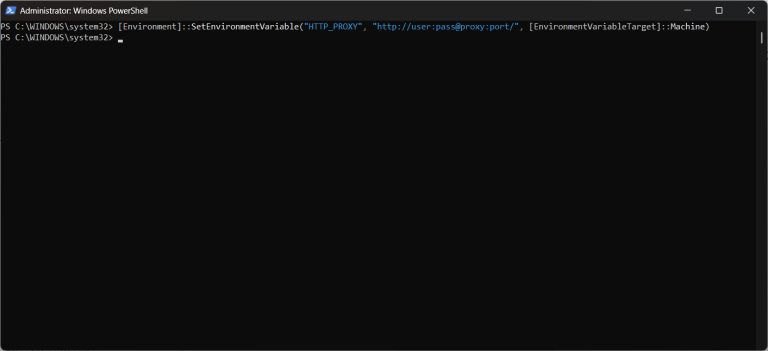
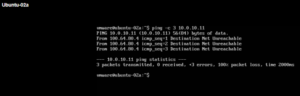
Get-Service docker Check the Docker CLI: Run the following command to verify that the docker command is available in your system’s PATH. Suggested read: Self-Hosting Docker vs Cloud-Based Docker Legacy…