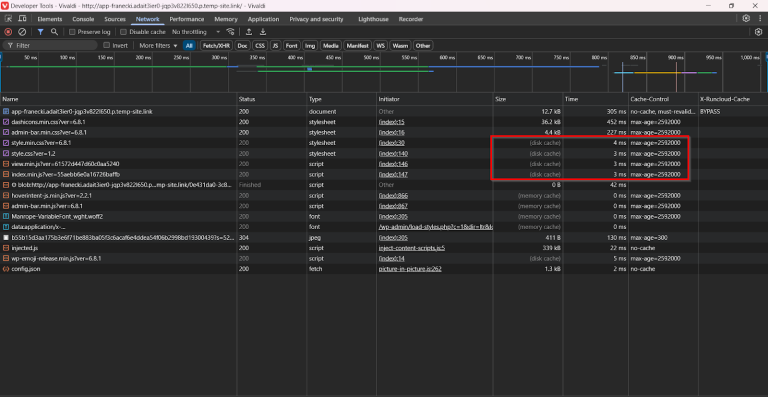
Server Cache vs. Browser Cache vs. Site Cache: What’s the Difference?
Caching speeds up performance by storing copies of frequently used data in fast-access memory. Instead of regenerating the same content on every request, the server or browser checks the cache…



![How to Use FTP to Upload Files to WordPress Without Password [Step By Step]](https://vmme.org/wp-content/uploads/2025/03/how-to-use-ftp-to-upload-files-to-wordpress-without-password-step-by-step-18-768x427.png)